Результат поиска по запросу: "vulnerability20assessment"

Sign displaying Vulnerability. Conceptual photo State of being exposed to the possibility of being attacked Voice And Video Calling Capabilities Connecting People Together
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Bishkek, Kyrgyzstan - March 14, 2019: Screen of unreal engine game installation software
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Vulnerability is written in white pencil on a black page.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

The computer crashed. Angry man having an error and system failure on his laptop while sitting on the couch
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Wooden cubes with cyber icons with the concept of network security vulnerabilities
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

white squares with security and Unsafe icons. the concept of safety takes precedence
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Text showing inspiration Unreasonable. Business concept Beyond the limits of acceptability or fairness Inappropriate Lady Pressing Screen Of Mobile Phone Showing The Futuristic Technology
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

puzzles and Safe And Unsafe icons. the concept of safety
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hacker performs a vulnerability scan on a laptop with a glowing digital interface. Clear details ...
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Finance and economics concept. On the table are reporting graphics and a thought plate, inside of which it is written - FEASIBILITY
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Conceptual caption Vulnerability. Word for State of being exposed to the possibility of being attacked Lady In Uniform Holding Tablet In Hand Virtually Typing Futuristic Tech.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Cybersecurity word. Cyber security concept, inscription on photo.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Concept of Volatility, Uncertainly, Complexity, Ambiguity write on sticky notes isolated on Wooden Table.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Wired lock for notebook protection
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Security word made of square letter word on gray background.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

close up of computer monitor progress loading bar
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
System protection from intruders. Persistent protection from hacker attacks on servers. Safety of critical infrastructure, hybrid wars in cyberspace. Internet threat monitoring. data security.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A white puzzle with a lock icon opened and one locked. padlock for cybersecurity. the concept of safety
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
puzzles and security icons passwords, phishing, malware, ddos and caution. data protection concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

3D illustration of computer keyboard with the script Vulnerability Assessment on two adjacent red buttons
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Forum, tablet and business people on stage with presentation for enhanced cybersecurity measures. Digital technology, conference and compliance managers with data encryption policies at seminar.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A man figure stares intently at a computer screen displaying a stark red You Lost message amidst lines of code, evoking a sense of tension and potential defeat in a cyber-security scenario.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

hexagon with cyber robber icons, caution and unlock. safety and security
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Close up of security symbol on a computer screen. Anti-virus software, “Securityâ€.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Privacy Access Identification Password Passcode and Privacy
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A man figure stares intently at a computer screen displaying a stark red You Lost message amidst lines of code, evoking a sense of tension and potential defeat in a cyber-security scenario.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Paris, France - Nov 10. 2017: enter a passcode when face id is not available new Apple iPhone XS Pro with Face ID virtual facial recognition function with anonymous hacker wearing a mask
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A man stands ready to defend against a digital threat, ensuring cybersecurity in todays interconnected world
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A laptop screen displays an error message, symbolizing failure in technology or systems.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hacker in dark hoodie analyzes vulnerability scan of server with outdated software. Clear details...
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
New York, USA - 1 May 2021: SeatGeek company website on screen, Illustrative Editorial
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Concept of Key and confidentiality Integrity Availability - CIA write on sticky notes isolated on Wooden Table.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Woman working with tablet with virus warning notification on screen and is choosing a management method from the options clean, quarantine, delete. Virus alert warning and secure on mobile device concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Cyber security interface with biometric and AI-powered protection system. Cyber security secures access, cybersecurity protects identity, cybersecurity detects threats, and defends data.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Woman hold laptop with virtual global with cyber security, Login, User, identification information security and encryption, secure access to users personal information, secure Internet access,
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Sign in, get access to a computer system as a guest. Log in message on a digital device screen, closeup view.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Laptop with green numbers on display. Smartphone displaying successful login with credentials user and password in the system. Technology communication, security privacy, hacker, cyber crime concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Image of network of connections with icons over businesswoman using laptop. Global connections, business, finance, computing and data processing concept digitally generated image.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

a hexagon with a lock icon opened and one locked. padlock for cybersecurity. the concept of safety
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A group of people are working on a laptop together. The man in the black shirt is looking at the screen and the others are looking at him. Scene is collaborative and focused
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Magnifier zooming in on padlock icon on blue background. Web secuirty concept. 3D Rendering
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

top view of multicolored cards with people icons on violet background, banner
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Conceptual hand writing showing Vulnerability. Business photo text Information susceptibility systems bug exploitation attacker Keyboard grey keys pink paper love idea thought computer hart
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

New york, USA - September 13, 2020: Udemy platform in internet browser on computer screen close up view
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

CYBER SECURITY Business technology secure Firewall Antivirus Alert Protection Security and Cyber Security Firewall
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Two businesswomen working on the project to protect cyber security of international company. Padlock Hologram icons over the table with documents.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

hexagon with lock and unlock icons. safety and security
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Virus warning alert on computer screen detected brisk cyber threat , hacker, computer virus and malware
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Broken padlock on closed laptop computer, concept for Internet and technology security breach or data theft
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Two businesswoman working with tablet in office room. Digital icons with network symbols and lock, global data protection. Concept of teamwork and security
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

An urgent digital notification or email in an inbox warns to verify an account, highlighting the pervasive risk of an online scam or phishing attempt targeting an individual's bank details.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Privacy and security mobile data concept. Smartphone with padlock icon and locked text. Modern technology, protection
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A vpn privacy safety smartphone secure browsing icon on mobile screen near coffee cup and paper highlight calm digital protection focus work
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Extreme close up on a glowing red triangular alert and an exclamation mark on a phone, indicating a critical system breach with cybersecurity risk
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Professional reviewing a credit risk assessment report on a tablet, highlighting financial warnings and financial metrics for risk evaluation.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Virus warning alert on computer screen detected brisk cyber threat , hacker, computer virus and malware
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Sign displaying Security Awareness. Business showcase educating employees about the computer security Abstract Giving Business Advice Online, Spreading Internet Presence
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Graphics Padlock For Web Data Information Security Application System
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Paris, France - oct 24, 2018: Clean Files sign on the computer display from the Dell Precision optimiser workstation software
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Panorama shot analyst team utilizing BI Fintech to analyze financial report with laptop. Businesspeople analyzing BI data dashboard displayed on laptop screen for business insight.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Close-up view of abstract digital data lines with vibrant colors, creating a futuristic and technological visual effect.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hand presents a digital shield with a vulnerability scan showing 100 percent and zero issues.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
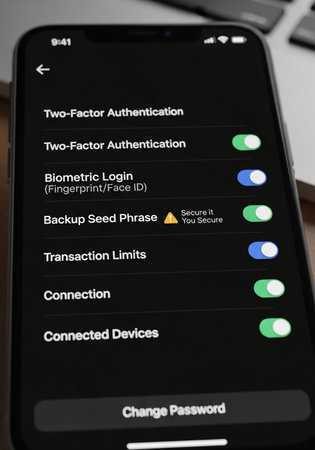
Smartphone displaying security settings including Two-Factor Authentication, Biometric Login, Backup Seed Phrase alert, Transaction Limits, Connection, Connected Devices, and Change Password option.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Kuala Lumpur, Malaysia, 24th July 2020: Close up Instagram application menu on smartphone screen. Instagram is a photo and video-sharing social networking service owned by Facebook.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

padlock on an internet cable connected to a laptop concept data protection cybersecurity. High quality photo
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
A white puzzle with a key and lock icon with an open red lock. the concept of safety
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Cyber security software show alert of cyber attack for protection snugly. Danger from virus, phishing and cyber fraud.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Cyber security importance. laptop and padlock in modern office - data protection and cyber attacks
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A man figure stares intently at a computer screen displaying a stark red You Lost message amidst lines of code, evoking a sense of tension and potential defeat in a cyber-security scenario.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Vulnerability as Weakness Concept with Falling Figure and Marker on Yellow Background
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Digital security prompt displayed on a laptop screen, requiring user verification to proceed with login. Emphasizes online privacy and protection
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Information Leak Prevention is shown using a text
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Two young intercultural programmers trying to solve technical problem in front of computers with critical error on screens
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

CYBER SECURITY Business technology secure Firewall Antivirus Alert Protection Security and Cyber Security Firewall
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Close-up of unrecognizable hacker engaged in hacking into security system on laptop green binary code on screen with sitting at desk in dark basement room, with blue neon lights.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Laptop, lock and paper with text PASSWORD ACCEPT. Hacking concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Work at home with computer and internet Laptop screen showing the login for online shopping. A man typing a keyboard key to use a computer network A laptop on a wooden table in a blurred background
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

CYBER SECURITY Business technology secure Firewall Antivirus Alert Protection Security and Cyber Security Firewall
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Mobile phone with messenger logo signal and lock on white background.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

LONDON, UK - APRIL 25TH 2017: The homepage of the official website for Vauxhall, the automobile manufacturer, on 25th April 2017.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hand hold the iPhone with iOS firmware update process on the screen. High quality photo
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

26 08 2019 Tula: laptop block on the phone and laptop display.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Cyber security protects against breaches, hacks, and network attacks using strong infrastructure and proactive digital defense strategies. Vouch
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A close-up view of a hand using a magnifying glass to examine a brightly lit padlock. The background is filled with a grid of smaller, less illuminated lock icons.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Virus warning alert on computer screen detected brisk cyber threat , hacker, computer virus and malware
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Image of cyber attack warning over hand of caucasian man in server room. global internet security, connections and data processing concept digitally generated image.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Wooden block with padlock icon on computer keyboard.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Vulnerability on the sticky notes with bokeh background
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

a magnifying glass in a red glove looks at a black screen
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hand Hacker touch laptop or smartphone and Touching in graph Screen code of a media screen on the White background, Technology Process System Business and hacks online concept, Copy space
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Conceptual hand writing showing Vulnerability. Business photo showcasing State of being exposed to the possibility of being attacked.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Woman hand hold credit card touch laptop with Security warning in graph Screen code of a media screen on the White background, Technology Process System Business and hacks online concept, Copy space
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Businesswoman hand using laptop with Data protection, Cyber security secure, information safety and encryption concept. internet technology and business concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A gloved hand holds a magnifying glass over a computer keyboard to reveal a distinct fingerprint on a key as part of a forensic investigation into digital security and cybercrime evidence.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Businessman uses capable laptop computer to manage cyber security system for defending computer virus , computer crime and hackers in order to maintain security of cyber business
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Image of connected icons over diverse coworkers discussing in tea break at office. Digital composite, multiple exposure, communication, ideas, beverages, drink and technology concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Image of scope scanning with cyber security text over diverse business people working at office. Global business, finances and digital interface concept digitally generated image.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A man figure stares intently at a computer screen displaying a stark red You Lost message amidst lines of code, evoking a sense of tension and potential defeat in a cyber-security scenario.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
London, United Kingdom - Mar 28, 2020: Man hand POV touching the touchscreen of a modern Microsoft Windows PC computer during the update of the OS operating system
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Mature woman using laptop at table. concept of online safety
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Поддержка
Copyright © Legion-Media.





